Reading The Docket
Ally came to me the other day upset about the TikTok case. One of her issues was that the AP was reporting that they couldn’t report more because it was “sealed”.
I found this to be unusual and went to the source to find out what is going on. What I found was somewhat different.
Ally pointed out that what I sent her, the docket, wasn’t something she understood.
This is a non lawyer’s take on reading dockets.
What is “The Docket”?
The docket is a record of a case. It contains the identifying information about the case as well as providing information on what court, panel, or judges will be hearing the case. It is relatively brief.
The biggest part is the “Proceedings and Orders”.
The Header
The header identifies the case. In addition, it helps track the case back in history as it moved through different courts.
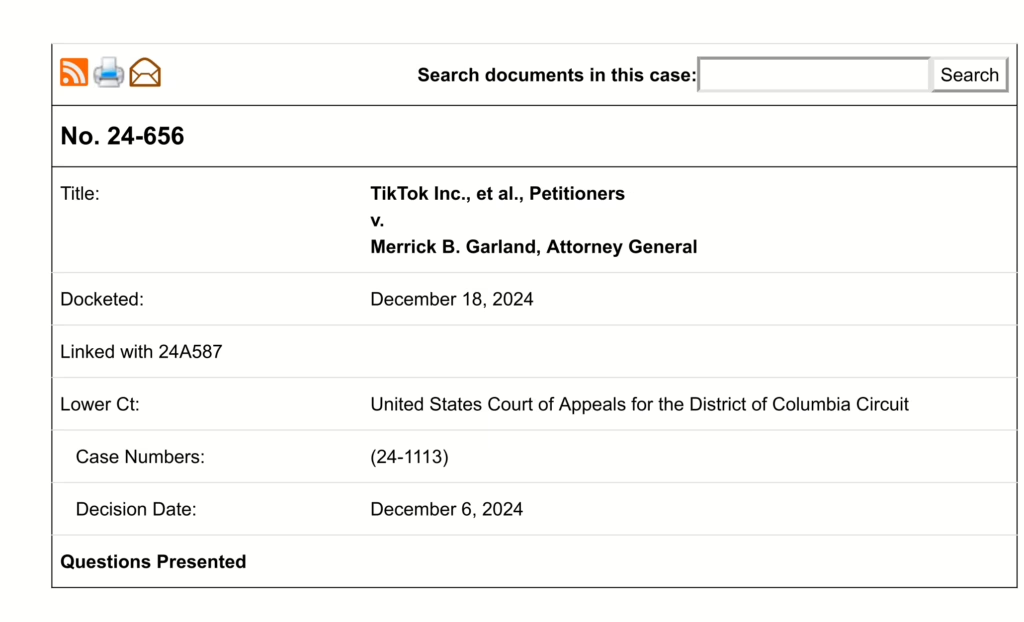
The title is the parties to the suit. The short title would be TikTok v. Garland. The date the case was docketed with the Supreme Court was December 18, 2024. The case comes from the D.C. Circuit Court. In the circuit court it had a case number of 24-1113.
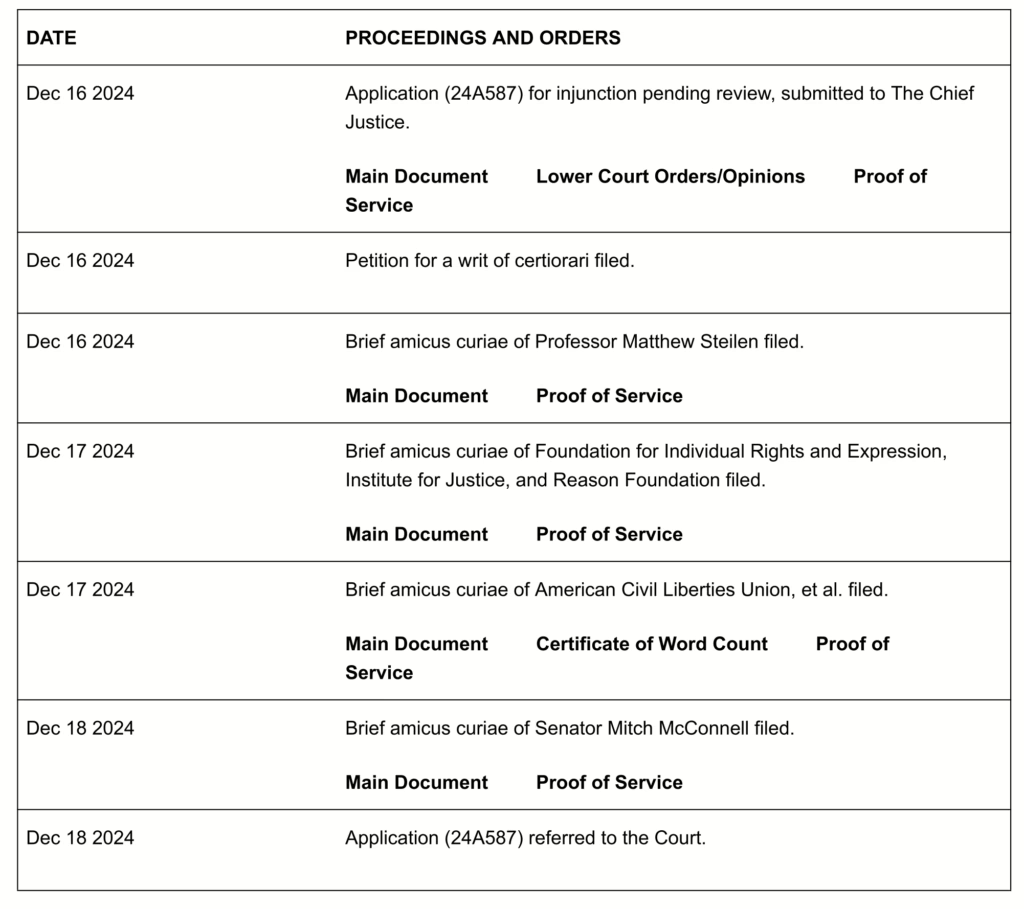
The first entry tells an interesting story. The first is that this case was submitted to the emergency docket, sometimes called the shadow docket.
When a case is placed on the emergency docket, it is assigned to one justice. Each justice is assigned a set of lower courts that they “supervise.” In this case, the D.C. Circuit Court is supervised by Chief Justice John Roberts.
The party petitioners are TikTok and ByteDance. They have “filed a motion” which is legal speak for “asked for something.” What they have asked for is an injunction against the enforcement of <q>Pub. L. No. 118-50, div. H (2024)</q>. This is the “Protecting Americans from Foreign Adversary Controlled Applications.”
In other words, they want the courts to stop the banning of TikTok.
To pull the information about motion, I read the “Main Document”. On the website, this is a link to the PDF of the document.
Because this case was put on the Emergency Docket, they are not asking the court to decide on the merits of the case, instead they are asking for an injunction until the Supreme Court has made their final decision regarding the ban.
Entry two says that they have also requested that the court hear the case, on its merits.
The next three entries are briefs by different groups of people called “Friends of the Court”, or “amicus curiae”. These are not parties of the case but instead are people who want to stick their two-cents in.
These briefs must be filed by a lawyer who is a member of the Supreme Court bar. In some situations, the people filing amicus briefs must get permission first.
What is a brief?
Simply put, it is a written argument. The person or group that files the brief feels that they have something important to say that might change the Court’s mind.
These briefs are all going to be arguing that the Supreme Court do something.
The respondents will often not argue at this point. To argue that the Court not hear the case is to make the case more important. Since the Court prefers to take cases that are important in the broad scheme of things, arguing that the Court not hear a case is arguing for the case to be heard.
On December 18th, the application, as 24A587 on the emergency docket, was referred to the Court.
This is the Court’s normal Wednesday conference.
The Justice discuss the cases which have been referred to them and decide as a group what they are going to do.
There is a deadline of January 19th for them to issue an order or opinion.
Things Happen
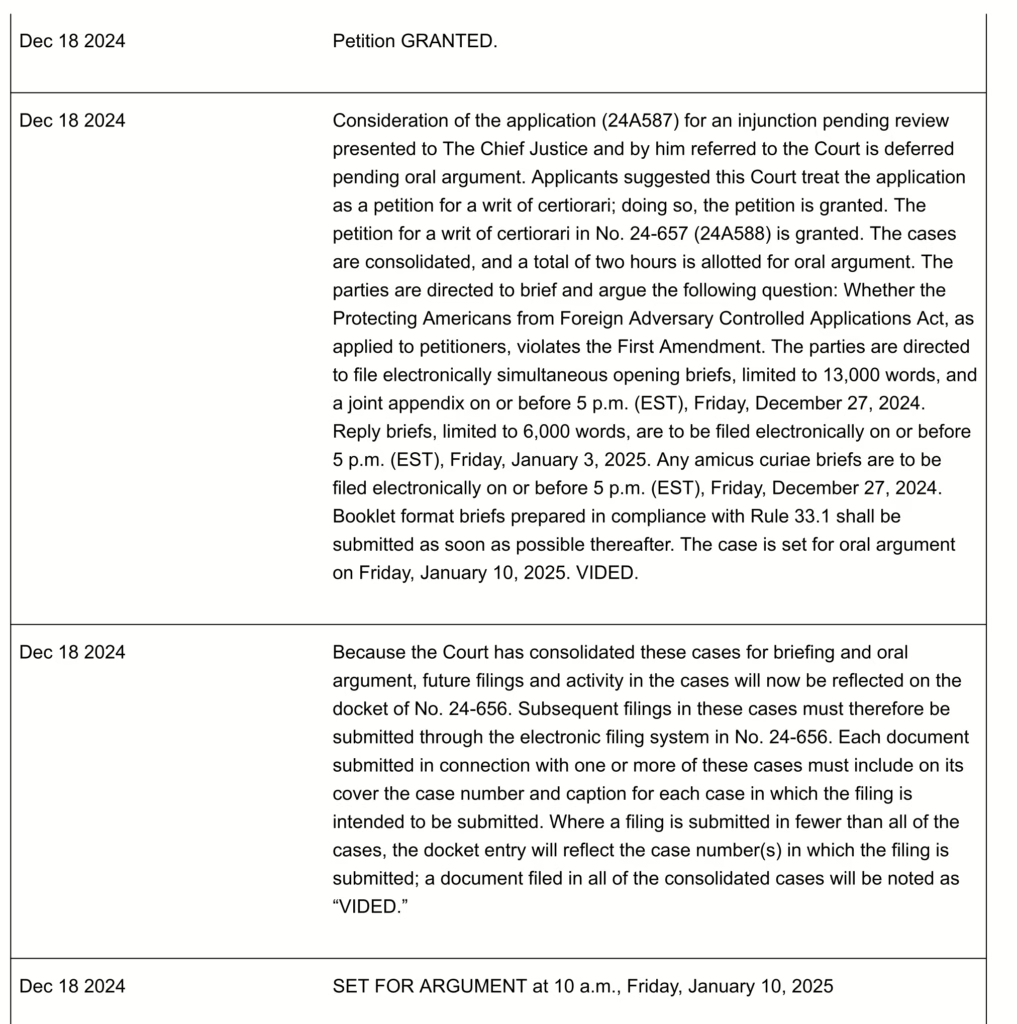
The petition is granted on the 18th. This means that the case went from not existing within the Supreme Court’s system to being granted cert in 2 days.
This is what “Emergency Docket” means. It has to happen now.
Now this particular case is on an expedited track. The Justices have given a word limit on the briefs. We will see later that there are “Certificate of Word Count” attached to many filings, stating they are within the limits set by the Court.
The time is also shortened. All the primary briefs are to be filed by December 27th. This is only 9 days after the granting of cert.
The court also says when oral arguments are happening.
The court also consolidated two cases. This is why we went from 24A587 to 24-656. The two original dockets were 24A587 and 24A656.
While the court said that oral arguments were on the 10th of January in their order. The official order is “SET FOR ARGUMENT at 10 a.m., Friday, January 10, 2025.”
Things Start Moving

We start to see the Amicus briefs start to arrive. They have until 1700 the 27th to get their briefs in.
We can tell that the people interested in this case have already prepared their briefs and are submitting them within a few days.
Our first entry is an order from the clerk of the court. They are telling the filer that they didn’t do it right. The submitted their brief with a word count, but the proof of service was incomplete.
The clerk will not accept the brief until the deficiencies are resolved.
Many Briefings and Orders
Outside the amici briefs, we have a “request”, which is Supreme Court speak for “order”, to the circuit court for a complete record. There is an “appendix” which is the compendium of all the briefs filed in the lower court(s?).
While the cases are combined, both petitioners request to argue separately. It will happen on the same day, one after another.
When reading these entries, the notation “(Distributed)” means that the filing has been given to the justices.
Many briefs are filed. The justices met and on the 31st granted the petitioners motion to argue separately.
All the replies were submitted on time.
One of the amici managed to mess things up so badly that they didn’t get their homework in on time. They asked the Court for an exception, the Court said, “no”.
Interesting Entry

This is the record of the cases before the D.C. Circuit Court. The records came in to parts. One part is open to the public, they other is sealed.
Sealed information can include things like financial details, personal identifying information (think SSN), or the identity of undercover or human sources. It can also include methods that the state doesn’t want public.
The Supreme Court can decide to unseal those records, but it isn’t going to happen. There is no need.
The Oral Arguments

The quick way to find out what happened on the 10th is to read the transcript.
If you want to spend 2 hours listening, you can listen to the oral arguments
What’s going to happen?
On the 17th, the Court has its next conference. They will discuss the cases referred to them, the cases distributed to them seeking cert, and cases where oral arguments have been heard.
They will come to a conclusion.
Once they decide, they need to write the opinion. If any justices are dissenting, they have to write their dissent.
Justices can write concurrences as well. This is when the justice agree with the opinion, but not the reasoning of the majority opinion.
Once all the opinions are finished, the opinion of the court will be released.
If the justices know that it will take longer to write the opinions than they have, they can issue an injunction. The injunction will put everything on pause until the Court can issue their opinion.
Where to From Here?
The path from here is working backwards. Given the circuit court and the docket number for that court, you can look up the docket on the Circuit Court’s website.
Of course, this doesn’t always work. To answer this, we use Court Listener to look up the case at the circuit court. The link I’ve given takes you to this case.
Within the circuit court docket, we find the same type of docket. Part of what we will find is a reference to the district court case.
All the oral arguments at the circuit level are available on the web. It can be difficult to find. Court Listener is your friend there as well.
Go have some fun reading documents.







